








Roundshield password generator and wallet

Description of Roundshield password generator and wallet
Roundshield provides three levels of security for your passwords:
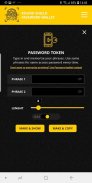
Password Token
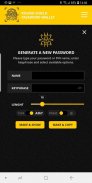
Generated passwords
Saved passwords
Round shield philosophy and logic is set in a way that user can use any of these modules independently of others (e.g. some will use only password tokens, others will use generated passwords and some will use all of the modules, and all use cases are perfectly OK).
Password token definitely is the most secure option in its implementation because Roundshield, in this case, does not store anything in your phone. Simply choose any two phrases that you can easily remember and Roundshield will generate a unique password for those phrases. Same phrases will always produce the same password, but you have to remember both of them since nothing is stored in your phone’s memory. Password token module does not require login using the secret phrase. Both phrases are case sensitive (e.g. combination PHRASE1 and PHRASE2 will produce different password token than combination phrase1 and phrase2).
Generated passwords are also very secure since its implementation also does not store the actual password in your phone in any form. It works pretty similarly to the Password token module, but instead of using (and memorizing) two phrases, you enter one phrase that will be saved in phone’s memory in encrypted form and used with your secret phrase for generating a unique password.
The secret phrase itself is also never stored in your phone’s memory, but instead, Roundshield saves an HMAC hexdigest of your secret phrase which enables it to verify your secret phrase each time you enter it but does not provide any methods to restore it.
The algorithm used by this module is different from Password token meaning that you cannot reproduce password generated with Password token in Generated password modules and vice versa (even if you use your secret phrase as one of the phrases for password token).
Saved passwords module acts as a password wallet and saves your existing passwords in an encrypted mode using Advanced Encryption Standard (AES) and encryption key generated upon your secret phrase (but not the secret phrase itself). Obviously, in this case, encrypted version of your password will be saved in your phone’s memory, but without your secret phrase (which is NOT saved anywhere) it will still require a powerful processor and vast amount of iterations to decrypt it. Actually, the required resources for this kind of attack are pretty much the same as for using “brute force” attack.
Device registration
Registering the device with the cloud is not required and does not affect the operation of any module, but enables the user to remotely delete all stored data from the phone in case of theft or losing it. Registration requires three parameters – username, server password (should not be the same as a secret phrase) and a name of the device that user will be able to recognize once there is a need to issue a delete command. Besides these data, Roundshiled will also send a model name (given by the manufacturer) and UDID (unique device identification – usually hexadecimal number) and neither of these two can be used to identify the user personally.
Once registered, the device will periodically check the cloud for a delete command and in case it receives it, deletes all stored data (passwords, phrases, etc.). This operation cannot be undone and all stored data will be lost. Furthermore, the application will stop working completely until it is uninstalled and installed again.
To issue a delete command, go to https://roundshield.dws.ba and log in using your cloud credentials.
Please note that none of the saved data are stored on the cloud (or anywhere else besides phone’s memory) and no one (neither user nor we as app developers) will be able to retrieve the passwords in case of deleting data or losing/forgetting the secret phrase(s).


























